With the ever-developing digitalization further enhanced by the global pandemic, new technological advances, and innovative network systems are constantly being introduced to our society. To remain competitive and continue to conduct business successfully, organizations incorporate technology and networks in their everyday activities more than ever before. In fact, according to Top Design Firms’ survey, 71% of small businesses have a company website, and 44% of those without a website plan to create one this year.
Although those shifts have many positive aspects, such as easier and faster customer service, they also propose cybersecurity risks for organizations. Retarus.com shares some quite alarming statistics connected to cyberattacks in the last couple of years, including the fact that in comparison to 2019 we’re witnessing 358% more malware attacks and 435% more ransomware attacks. Therefore, businesses need to take the necessary measures and protect themselves and their clients against cybercriminals. The first step to the cybersecurity of any company, however, is outlining the key vulnerabilities associated with the organization’s specific industry and business type. To do this cybersecurity specialists conduct vulnerability assessments.
What is a vulnerability assessment?
Essentially, a vulnerability assessment is an ongoing process that identifies the security vulnerabilities of a given company’s network system, IT applications, and infrastructure by performing security scans either manually or with the help of automated testing tools.
In other words, it is used to determine the extent to which a technology asset could be threatened by a potential circumstance or event. Once the threats and the weak spots are outlined, cybersecurity specialists create a vulnerability assessment report that includes detailed information about the findings. Vulnerability assessment reports enable organizations to gain a clear understanding of their security posture and take the necessary actions to mitigate or eliminate any cybersecurity risks they may be faced with.

When performing vulnerability assessments cybersecurity specialists not only quantify the vulnerabilities but also analyze and prioritize them based on predefined risks. Moreover, vulnerability assessments are a component of the company’s holistic security program to maintain compliance with popular industry standards, like for example ISO27001, PCI DSS, SWIFT Customer Security Program (for financial institutions), and HIPPA (for the healthcare sector), and many more.
It is important for business owners to differentiate between penetration testing and vulnerability assessment, as although similar, each of both services has a unique nature. While the latter can help outline vulnerable spots in the systems of a given organization via scans, penetration testing goes much deeper into those vulnerabilities to determine their potential impact. In this sense, vulnerability assessment and penetration testing complement each other and can be used together to gain a better and more comprehensive understanding of the critical threats for the organization.
Types of Vulnerability Assessment
In terms of the examined areas of a company’s infrastructure, there are three main types of vulnerability assessments:
-
External Scans
They aim to outline vulnerabilities in the external IT infrastructure which can be accessed from anybody through the Internet. Cybersecurity experts conduct external vulnerability assessments without having physical access to the scanned network.
-
Internal Scans
Internal Scans are used to detect vulnerabilities in the network of a given organization and, unlike external scans, are performed with full access to the scanned organization’s internal network. These types of scans can outline security gaps inside a company’s network and detect already existing malware, which has penetrated the defense systems.
-
Environmental Scans
These scans aim to outline vulnerabilities connected to the specific operational technologies a given organization uses, for example, cloud services, mobile devices, and IoT.
Additionally, vulnerability scans can also be classified based on the assets they examine:
- Network-based scans: aim to detect if any unauthorized devices or users are connected to the network
- Host-based scans: aim to outline vulnerabilities on workstations, servers, or other network hosts
- Wireless scans: aim to detect unauthorized open Wi-Fi networks in the organization’s infrastructure
- Database scans: aim to discover vulnerabilities in the database of a given organization
- Application scans: aim to detect vulnerabilities in web- and mobile-based applications
The vulnerability assessment process
Any vulnerability assessment regardless of its type is conducted by following the same steps: Planning, Asset Discovery, Conducting the Scans, Analyzing the Findings, Creating a Remediation Plan, Recommendations.
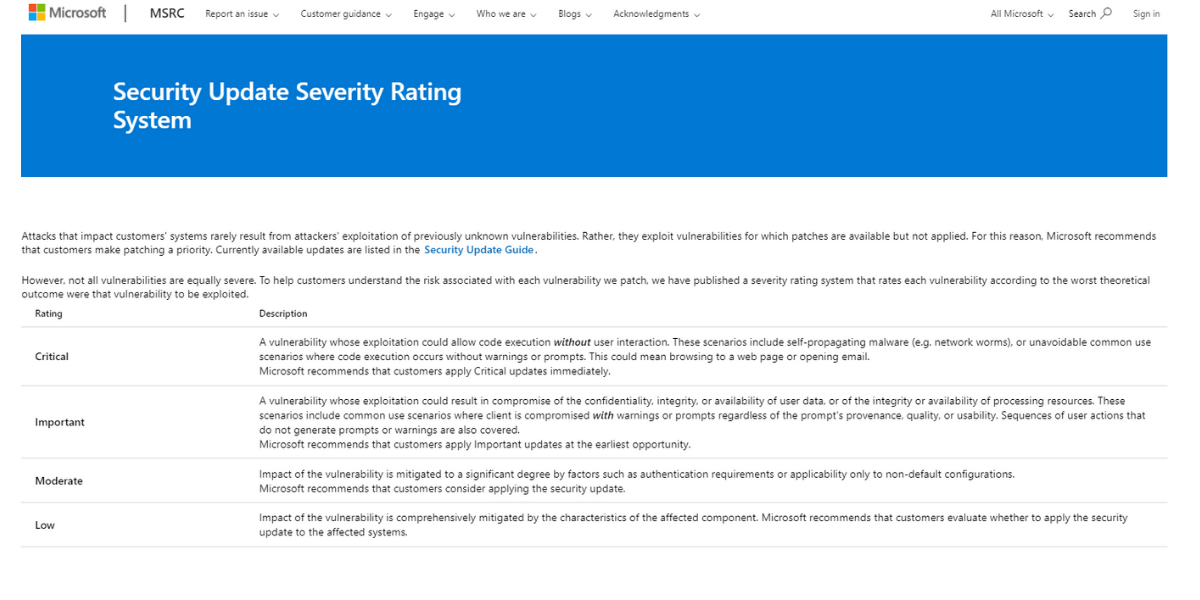
During the planning stage, cybersecurity experts will research the organization’s network and environment to familiarize themselves with the specifics of the particular business. Within the Asset Discovery process, they will also outline the main goals of the vulnerability assessment and will determine which assets need to be scanned in order for the assessment’s objectives to be met. Then, the cybersecurity experts will either use manual or automated tools to scan the organization’s network. Usually, the scanning will result in a list of vulnerabilities and the level of their severity according to the Common Vulnerability Scoring System (CVSS). CVSS is a published standard used by organizations worldwide. It is a system that produces a numerical score reflecting the severity of a given vulnerability and labeling it as either low, medium, high, or critical.
Once the scans are completed and the vulnerabilities, as well as their severities, are outlined, the experts will then analyze the findings of the scans. They will rule out any false positive signals, evaluate and interpret the results and the risks, and outline the possible causes of the vulnerabilities. Last but not least, the cybersecurity experts will create a thorough report and an appropriate mitigation plan that focuses on the highest severity priorities and that is tailored to reflect the unique nature of the organization and its operations.
Furthermore, vulnerability assessment is and should be an ongoing process.
A single assessment can only provide you with a snapshot of your security posture at a given moment in time and does not guarantee that after a few months your network will be still facing the same vulnerabilities (or that it will be still secured once you’ve implemented the mitigation or remediation solutions). Therefore, to maintain a good security posture and to keep compliant with the industry regulations organizations need to continuously conduct vulnerability assessments. Deriving from these facts, it is safe to say that the final step of vulnerability assessment is repetition.
Why is vulnerability assessment important?
One of the key benefits of vulnerability assessment is the fact that it helps organizations improve their cybersecurity visibility and gain valuable information about the threats they may be faced with. Visibility is crucial because you cannot protect what you cannot see. According to Edgescan’s vulnerability statistics report from 2020, 64% of professionals admitted to not being fully aware of their organization’s web applications or end-points. Furthermore, nearly 68% believe their visibility is ‘average’ while acknowledging they do not monitor some connected devices. This data emphasizes the significant lack of visibility into assets for most organizations, which is alarming but can be improved by conducting regular vulnerability assessments.
Furthermore, Edgescan’s 2021 vulnerability statistics report points out that 50% of the vulnerabilities discovered in internal web applications were rated as high or critical risk, while external networks have a high or critical risk density of 32%. Additionally, the report shows that the average time needed for mitigating high-risk vulnerabilities is 84.4 days while critical-risk vulnerabilities are usually mitigated within 50.9 days. During this time cybercriminals can take advantage of the weak spots in the organization, which can lead to data breaches and different types of cyberattacks. Consequently, this could cost the business even more time and money to recover. Therefore, the faster those vulnerabilities are detected, the quicker they will be resolved and won’t propose any threats to the organization.
Vulnerability assessment can not only help businesses ensure the safety of their organization, but it can also serve as proof of the security posture of a given company. Moreover, vulnerability assessment is a key part of becoming compliant with certain industry regulations such as and not limited to ISO27000, PCI DSS, SWIFT Security Program, and HIPPA, as mentioned above. Last but not least, vulnerability assessments can help organizations evaluate the risks third-party service providers propose to the business.
Don’t hesitate to contact us if it’s time for evaluation of the vulnerabilities of your company’s network, or if you simply have any questions about vulnerability assessments and cybersecurity as a whole. 3Cyber-Sec’s team is always ready to help by providing tailored solutions to organizations operating in diverse industries. Our expertise and collaborative approach allow us to focus on and respond to the specific needs of each of our clients.

