After the global media outburst during the last few months, it is safe to say that the SolarWinds cyberattack is fairly popular and many people know about it today. However, this does not change the fact that no one was prepared for the unprecedented hack while it was taking place.
We’ve witnessed several US federal agencies and thousands of businesses being compromised with (possibly) a single supply chain cyberattack targeting SolarWinds – a company that provides network monitoring products to top USA state-owned and public organizations. What’s unique about this attack is its sheer magnitude. It was executed in a professional and precise manner with the help of complicated techniques. The cybercriminals behind it were highly knowledgeable and experienced hackers. They used sophisticated methods that enabled them to attack multiple companies while remaining undetected for at least 10 months.
While the investigation as to what exactly happened, who is responsible, and what will be the consequences is still ongoing, we’re here to take a look at this curious case and shed light on the key findings available to the public so far.
How was the SolarWinds cyberattack performed, who was compromised, and who is responsible?
The SolarWinds hack was a supply-chain attack.
Cyberattacks of this kind can compromise the security of a given organization through third-party providers who have access to the organization’s network, systems, and data. In this case, the hacked third-party provider was SolarWinds. As a result, over 18 000 networks, systems, and data were compromised. Additionally, more than 200 private businesses (including big names such as Microsoft, Cisco, FireEye, and Intel) and several federal agencies including the US Department of Commerce, the US Department of Homeland Security, the US Department of the Treasury, the National Institutes of Health, the US Department of Energy, and the National Nuclear Security Administration were also affected by the attack.
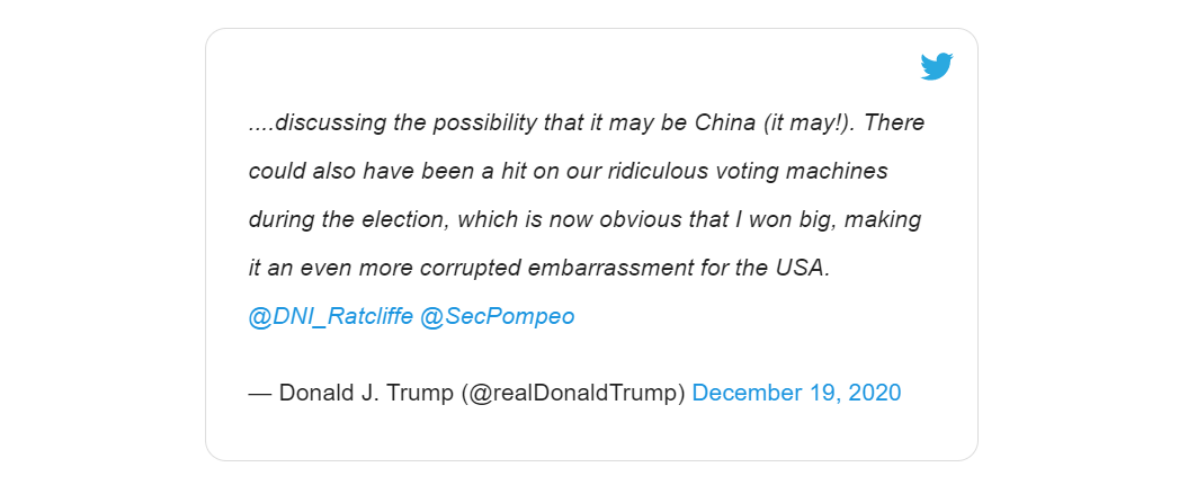
Although it is still not confirmed who is responsible for the hack, US government officials and popular media websites such as The Washington Post, have claimed that the attack was performed by a Russian hacking group referred to as APT29 or Cozy Bear. The idea that the hacking group was state-funded and a part of Russia’s foreign intelligence service was also mentioned to the public. Donald Trump, on the other hand, posted a tweet about two weeks after the attack’s discovery in which he expressed his beliefs that China may be the one behind it. That said, for the time being, there is no proof that either of the two countries was involved.
According to Microsoft, there were more than a thousand cybercriminals who participated in the creation of the SolarWinds cyberattack and they must have had incredible skill sets. It is believed that the initial hack took place way back in September 2019 when the attackers used a highly sophisticated malicious software referred to as SUNSPOT to insert the now-infamous SUNBURST malware into SolarWinds’ IT management software product Orion. The cybercriminals were able to replace one of Orion’s source files and add the SUNBURST backdoor code to it, which allowed them to bypass the cybersecurity defense systems that were in place, gain access to SolarWinds’ networks, as well as to SolarWinds’ clients’ networks, transfer files, execute files, profile the system, reboot the machine, and disable system services. As FireEye shares:
The malware masked its network traffic as Orion Improvement Program (OIP) traffic and stored reconnaissance results within legitimate plugin configuration files, enabling it to blend in with legitimate SolarWinds activity.
The SUNBURST backdoor enabled the attackers to introduce another malicious software, which was used to trojanize a series of Orion update fails, which were released by the IT service provider SolarWinds between March 2020 and June 2020, as CSO shares. Once they gained access to the compromised systems, the hacker group was careful not to leave any traces and preferred to steal and use credentials to move laterally through the networks and establish remote access.
Detection and Response
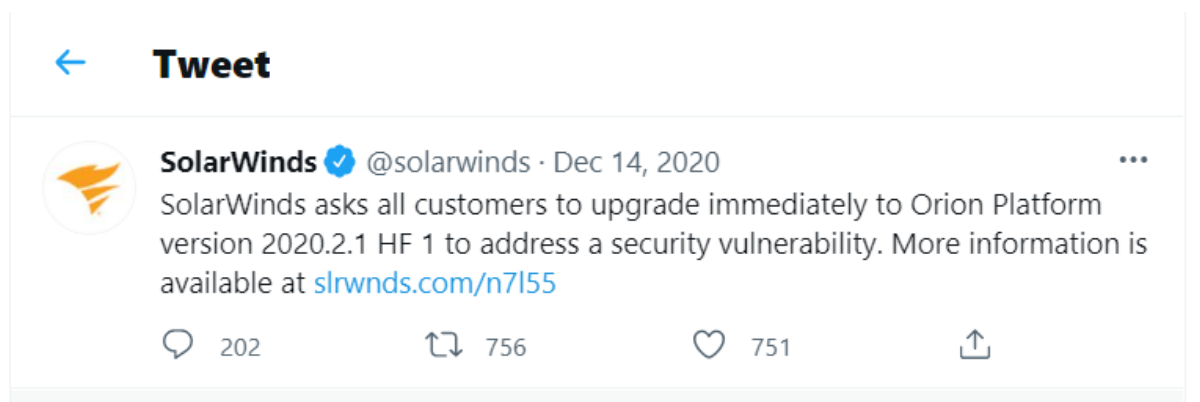
The hack was first detected by the cybersecurity company FireEye at the beginning of December 2020. FireEye discovered that there has been unauthorized access to their systems and traced back the trail to SolarWinds. On the same day, 13th of December 2020, the USA’s Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive with instructions for mitigating SolarWinds Orion Code Compromise. Furthermore, SolarWinds started informing its clients via Tweets that they need to immediately upgrade the Orion Platform to another version to address the vulnerability. Shortly after, SolarWinds introduced two additional updates that were meant to serve as “hotfixes” along with instructions for their implementation.
In mid-December, FireEye discovered a “killswitch”, which could block the functions of the malware and prevent it from doing further harm. However, as darkreading.com shares:
FireEye’s fix wasn’t effective for networks where the attackers might have already deployed additional persistence mechanisms.
The scope of the attack became clear by the end of December when the majority of the victims were named in the press. At the beginning of January 2021 a joint statement by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Office of the Director of National Intelligence (ODNI), and the National Security Agency (NSA) was released. The statement informed that the National Security Council staff has stood up a task force construct composed of the FBI, CISA, and ODNI and supported by NSA. The task force group was named Cyber Unified Coordination Group and its main purpose was to “coordinate the investigation and remediation of this significant cyber incident involving federal government networks”. On the 6th of January CISA issued supplemental guidance in relation to the emergency directive for mitigation of the SolarWinds hack. Furthermore, the security agency updated the directive with additional information and instructions once more – on the 22nd of April.
At the end of January 2021, CISA issued a malware analysis report with technical details about the malicious software used for the attack, while SolarWinds also published a security advisory with information about the company’s response to the incident. Around one month later, in late February, the national security adviser Jake Sullivan announced during an interview for CNN that the US administration is working towards addressing those responsible for the attack within weeks:
We are in the process now of working through a series of steps to respond to Solar Winds, including steps that will hold who we believe is responsible for this and accountable, and you will be hearing about this in short order. We’re not talking about months from now, but weeks from now, that the United States will be prepared to take the first steps in response to solar winds.
The cyberattack was so sophisticated that it became the reason for several council hearings the first of which was held on the 23rd of February by the US Senate intelligence committee. During the hearing executives from SolarWinds, Microsoft, FireEye, and CrowdStrike discussed the attack. As Associated Press informs, the CEO of FireEye, Kevin Mandia, told the Senate that his company has had nearly 100 people working to study and contain the breach since they detected it in December 2020. On February 26th the executives from SolarWinds, FireEye, and Microsoft were summoned once more to testify before a joined house hearing held by the US House of Representatives’ Oversight and Homeland Security Committees. The main topics of the hearing were concerned with how and why did the SolarWinds hack happened, was classified government information compromised, and what are the existing vulnerabilities to the cyber supply chain.
At the beginning of March 2021, CISA issued another set of guides on remediating networks affected by the SolarWinds hacks and encouraged affected organizations to review and apply the necessary guidance. At the end of the same month, news broke that the SolarWinds hacker group also managed to access email accounts belonging to the Trump administration’s head of the Department of Homeland Security and DHS cybersecurity staff members whose jobs included hunting threats from foreign countries, as Associated Press shares.
One of the last actions in response to the SolarWinds cyberattack was undertaken a couple of weeks ago when on June 21st the US Securities and Exchange Commission started an investigation that aims to determine if any of the compromised companies failed to disclose that they had been affected by the SolarWinds hack, as reported by Reuters.
Consequences of the SolarWinds Cyberattack
Even now, one year and nine months after the initial SolarWinds cyberattack and seven months after the hack’s discovery, the investigation and remediation activities continue. According to Brandon Wales, the acting director of CISA, officials will have fully secured the compromised government networks not earlier than 2022. Additionally, Wales said that even fully understanding the extent of the damage will take months and it could take up to 18 months before the US government recovers from the SolarWinds hack:
There are two phases for response to this incident. There is the short-term remediation effort, where we look to remove the adversary from the network, shutting down accounts they control, and shutting down entry points the adversary used to access networks. But given the amount of time they were inside these networks—months—strategic recovery will take time.
Of course, the biggest, scariest, and most obvious outcome of the SolarWinds attack is the fact that thousands of private and several government organizations were compromised. It shouldn’t come as a surprise that according to a survey by Domain Tools, 96% of the 200 respondents, amongst which global security specialists and executives, were concerned by the SolarWinds cyberattack. Furthermore, 60% of the impacted respondents said they were still not sure whether the compromised data was breached and 21% admitted that their sensitive data was in fact breached.
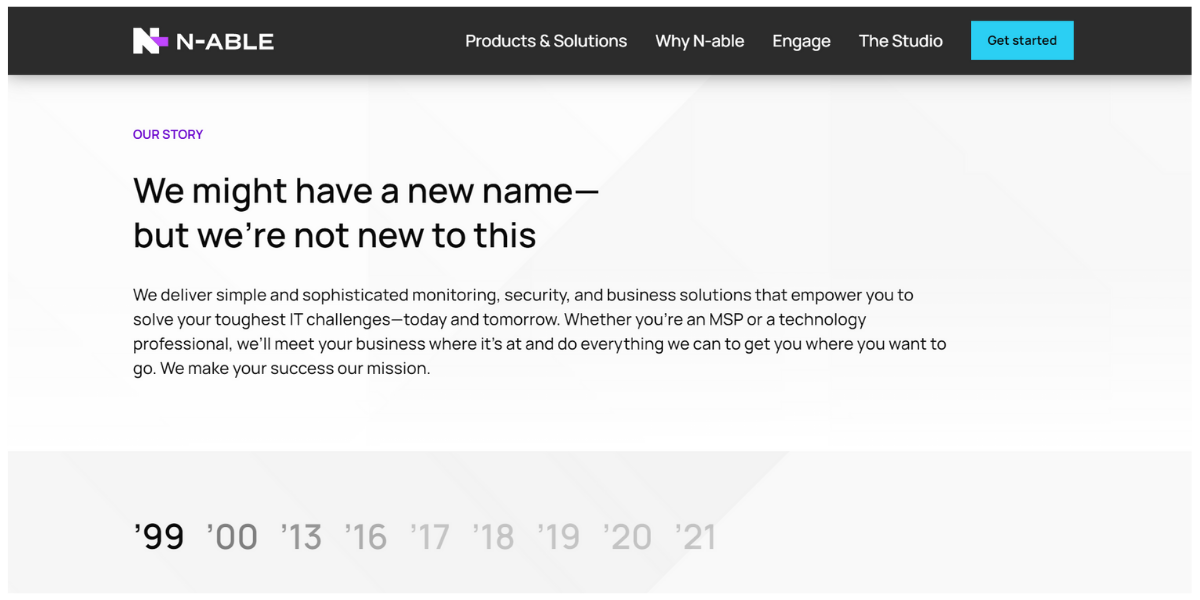
It is not a secret that cyberattacks often lead to a damaged reputation and the SolarWinds case isn’t an exception. SolarWinds was planning to spin out SolarWinds MSP – another service offered by the company which provides monitoring and management IT solutions. After the attack, however, SolarWinds decided to re-brand their MSP business, which is now known as N-able. According to channele2e.com, although company officials have stated that the N-able business and associated MSP software were not involved in the Orion attack, the January 2021 sales in the MSP software business were slightly impacted by it.
The attack is also going to cost a lot of money. According to MSSP Alert, SolarWinds said that it already had to pay $3.5 million in one-time expenses related to the hack. Furthermore, the company’s executives said that they estimate costs of $20 million to $25 million related to the hack and going towards upgrading the company’s security posture in 2021.
No one is safe against innovative cyberattack methods – that is the essential lesson to learn from the sophisticated SolarWinds hack. Businesses have to be cautious when trusting third-party providers regardless of how well-known their brands are. Furthermore, cybersecurity experts and companies should continuously strive to better their defense mechanisms so that they can respond adequately and mitigate future risks. Last but not least, organizations need to achieve greater visibility concerning the vulnerabilities of their systems and networks.
If you need help with identifying the vulnerabilities of your systems or if you seek expert cybersecurity advice, contact us for a free consultation. 3Cyber-Sec is a boutique cybersecurity consultancy company. Our primary focus lies in the development of cyber and information security control frameworks, infrastructure as well as vulnerability management solutions.

