Welcome to the first post from 3Cyber-Sec’s monthly rubric “Experts’ Talk”! Each month we’ll be talking to recognized cybersecurity experts with the goal of shedding light on some of the key topics connected to the cyber world. Our guest experts will provide exclusively for our readers their unique perspectives on diverse questions in connection to their field of expertise. With years of experience and dozens of solved problems, they will give you essential advice that can save your business and help you stay afloat even in your hardest times. Make sure you don’t miss any publications from our sequence so you can stay on top of the latest trends and insights from the cybersecurity world and ensure your business’s safety.
Today, together with 3Cyber-Sec’s business development manager and certified cybersecurity consultant Todor Kunev, we’ll be getting to the bottom of phishing attacks and the dangers they propose for businesses and individuals. Todor Kunev is an exceptional industry professional, capable of devising and implementing cybersecurity scenarios to strengthen cybersecurity and safeguard sensitive information and systems for his clients. To achieve his current level of expertise, Todor has spent years working towards obtaining his licenses and certificates some of which include CDPSE, CISM, CCNP, and CCNA. He was eager to share his take on phishing with us, hoping that his advice might elevate some of the misunderstandings connected to the topic.
Let us explain what phishing is. It has nothing to do with the relaxing lake-house weekend you might be imagining. Although the word sounds just like the well-known hobby of fishing, phishing is not about you catching fish, but rather it’s about you being preyed upon by cybercriminals. In essence, this cyberattack type uses socially engineered emails (or in some cases text messages and voice calls) with the malicious intent to direct users to dangerous websites, distribute malware, collect credentials, and more.
As Todor Kunev puts it:
“All phishing attacks aim to create a sense of urgency, provoke users’ interest or inflict fear. Once they’ve succeeded in grabbing users’ attention, cybercriminals usually propose a solution to the “urgent matter” in the form of a downloadable document or a link leading to a malicious website.”
It is one of the most popular cyberattack methods which is widely used today. In 2020 alone, 75% of organizations had experienced phishing attacks, according to research conducted by Proofpoint. Furthermore, 74% of the attacks that targeted businesses in the US were successful. This data is concerning especially given the fact that phishing attacks could cost organizations $3.8 million on average, as reported by retruster.com. Therefore, businesses should do everything in their power to prevent this from happening to their organizations.
Types of phishing attacks
There are quite a few types of phishing attacks depending on the communication channel and method used for the attack, as well as on its target. In terms of communication channels, we can outline four main types of phishing attacks – email phishing, smishing, search engine phishing, and vishing. As reported by Tessian, the most popular of them is email phishing with 96% of all attacks belonging to this category. The other 3% and 1% of the attacks were delivered via malicious websites (search engine phishing) and via smartphones (smishing and vishing) respectively. This data is also supported by Proofpoint’s research, which found that in 2020, 66% of the surveyed organizations experienced targeted phishing attacks, 61% of businesses faced smishing attacks and 54% of the respondents say they were targeted by vishing attacks.
“Email phishing occurs when cybercriminals impersonate a person or a business and send you an email with the goal of tricking you into clicking on a malicious link or downloading an infected attachment. Smishing and vishing are both different types of phishing, however, they are not used to target users via email. Vishing is referred to when cybercriminals call you on the phone pretending to be an employee from a well-known company, Microsoft for example, and request that you give them your personal details or payment information. When you receive a text message with malicious links, then you’ve been targeted by a smishing attack. The word is formed from the combination between “SMS” and “phishing”. Last, but not least, search engine phishing, or “SEO poisoning” as we sometimes call it, is when hackers create malicious websites and try to rank them on the first pages of legitimate search engines such as Google. Those websites could offer irresistible product deals intending to collecting as many of the users’ card details as possible, or they could look like an exact copy of another website, again aiming to deceive the user into giving his or her personal information away.” – explains Kunev.
In terms of the target of the attack, there are two main types of phishing – whaling and spear phishing. They are both similar in the sense that they target specific groups of people. Spear phishing occurs when hackers strategically direct their malicious message towards a particular organization or a particular employee in a selected company. Whaling, on the other hand, refers to cybercriminals who target the CEOs or the “big fish” in a given organization.
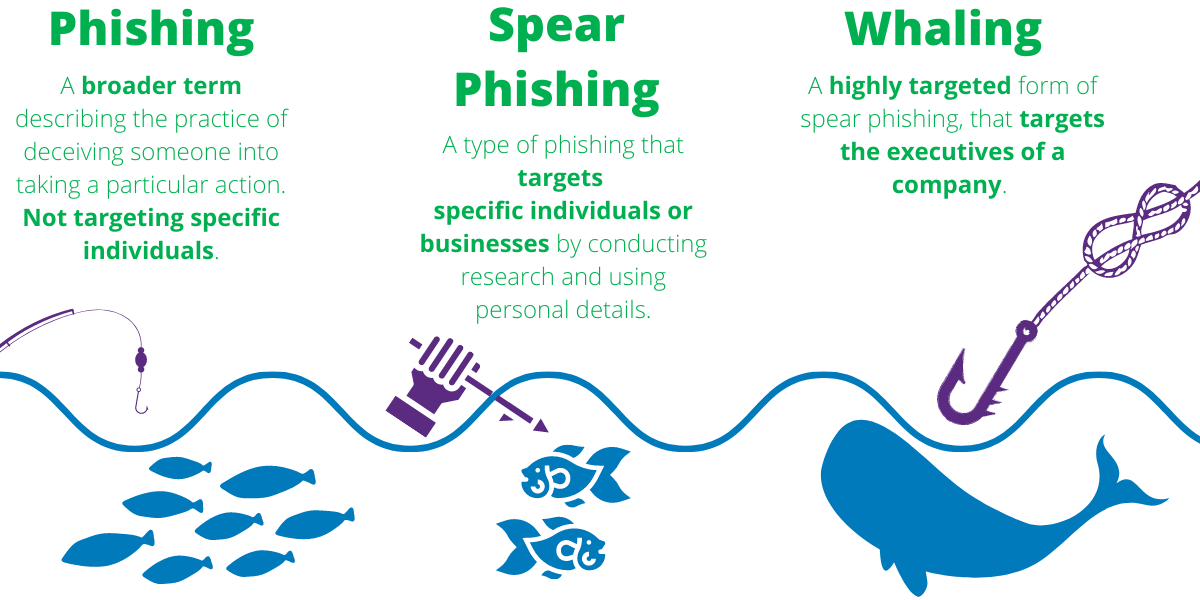
In his career as a cybersecurity expert, Todor Kunev has witnessed both whaling and spear phishing. According to him, those methods are particularly concerning because the messages they use are specifically crafted for the recipient (attack’s victim), which means the cybercriminals had to research their target.
“Cybercriminals often research names and company roles of employees working in the targeted organization, they even go as far as stalking their social media profiles and browsing through their friends’ lists. The goal is to produce a highly targeted, highly personal message, which prompts the victim to reveal sensitive information (both personal or in relation to the business), make a bank transfer, or alter documents to the cybercriminal’s benefit.” – says Kunev.
Therefore, it is extremely difficult to recognize targeted phishing attacks such as spear phishing or whaling. In fact, 97% of the users are unable to recognize a sophisticated phishing email. However, if you’re not recognizing a problem, it doesn’t mean it’s not there.
Consequences of phishing attacks
According to Proofpoint’s research, due to phishing attacks in 2020 businesses were left to deal with data loss (60% of the respondents), compromised accounts (52% of the respondents), ransomware infections (47% of the respondents), malware infections (29% of the respondents), and financial loss or fraud (18% of the respondents). The consequences of phishing attacks also include legal trouble, reputational damages, and intellectual property loss. This includes trade secrets, research findings, new developments, and other valuable data, which often cost the targeted organization years of work and thousands of dollars of research. However, according to Todor Kunev, one of the most dangerous aspects of phishing is the fact that businesses take too long to even notice they were attacked.
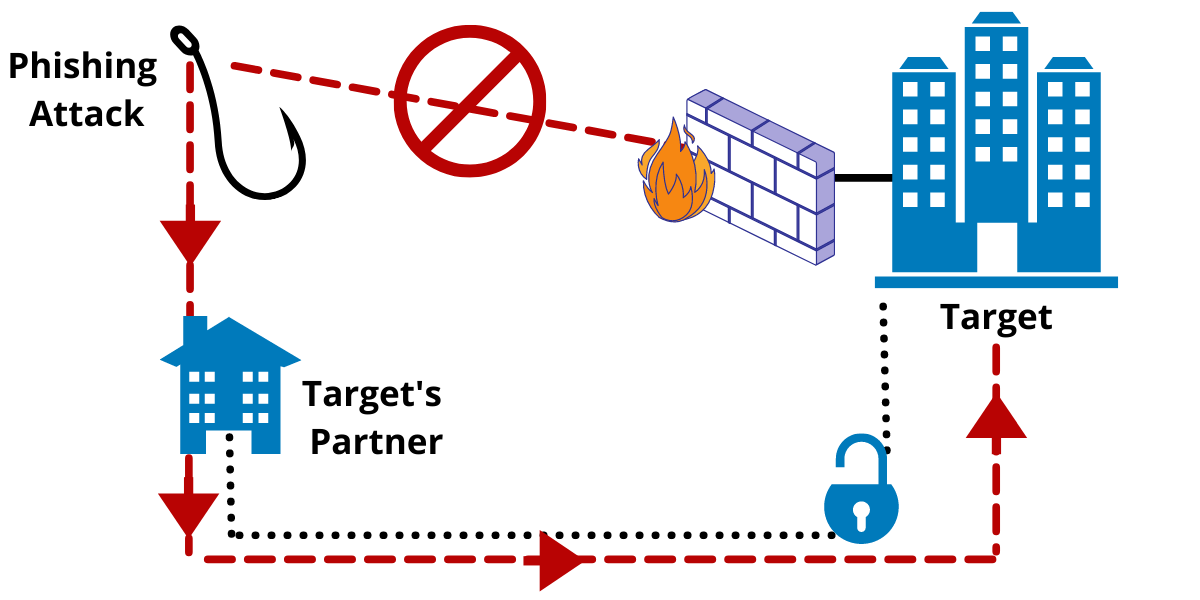
“It’s not uncommon for cybercriminals to target a business partner of yours in order to access your data. When the phishing attack is successful they can easily get hold of your network, because you and your employees perceive the already infected partner as a trusted source. Once the attackers gain initial access to your network through a given endpoint (one of your employees’ computers, for example) they may impersonate a legitimate user and continue to move laterally through your network. This means that even if you detect the initial point of access, you may not even notice or know that the cybercriminal is going through your files and systems and mapping them out until they find something of interest.” – shares Todor Kunev.
According to fortinet.com, it takes approximately 280 days to identify and contain an average cyberattack. In the meantime, businesses lose $2.9 million a minute due to cybercrime, as reported by riskiq.com. We don’t even want to do the math on this one.
How to spot a phishing attack?
Phishing attacks can often be easy to spot because of poor spelling and grammar, or because of poorly created links, which can hint that the web pages they lead to are fabricated. Some of the key clues of a phishing attempt are:
- The message is informing you that you need to take immediate action concerning a given matter
- The message is sent from a public email domain (simply @yahoo.com, for example, as opposed to @3cyber-sec.com)
- The domain name is spelled incorrectly
- The email contains grammatical, spelling, and/or punctuation mistakes
- The email includes a suspicious link or attachment
However, targeted phishing attacks such as spear phishing or whaling can be difficult to recognize. That is why it’s important to educate your employees about the warning signs and appropriate action plans in case they are targeted. Todor Kunev’s expert opinion is that staff awareness training should be done as regularly as possible, but not farther apart than 3 months:
“In the digital transformation journey, our customers’ exposure change requires the implementation of robust security capabilities to mitigate risk-shift and enable the business’s vision. It is crucial for businesses to invest in staff cybersecurity awareness training because more often than not, your employee serves as the middleman between a cybercriminal and your organization. Your employees need to be able to recognize the warning signs and avoid opening suspicious emails.” adds Kunev.
If you don’t know how to organize staff cybersecurity awareness training, you can always contact us for advice. 3Cyber-Sec’s team is composed of certified cybersecurity consultants, who can help you stay safe in the cyber world. We are determined to craft a tailored security solution for your specific needs.

